Mastering Managed Cloud Security Services
What are MSSPs?
Managed Security Service Providers(MSSPs) provide comprehensive protection for organizations' cloud environments, including infrastructure, applications, and data. As businesses increasingly adopt cloud technology to stay competitive, they also need to ensure the safety and security of their digital assets. Cloud security is a complex area that requires specialized knowledge and expertise to protect data, applications, and infrastructure from the evolving threat landscape. This is where managed cloud security services come into play.
Managed cloud security services provide organizations with comprehensive protection for their cloud environments. These services are designed to address the unique challenges and risks associated with operating in the cloud. By outsourcing their security management to a trusted third-party provider, organizations can ensure the continuous monitoring, incident response, and compliance management necessary to protect their cloud assets.
Managed cloud security services offer several key benefits. First and foremost, they provide organizations with round-the-clock monitoring and incident response capabilities. This means that any potential threats or security incidents can be detected and addressed in real time, minimizing the impact on the organization's operations. Additionally, managed cloud security services help organizations achieve compliance with industry regulations and standards, ensuring the protection of sensitive data and avoiding potential penalties.
By partnering with a managed cloud security provider, organizations can also benefit from the expertise and specialized knowledge of security professionals. These providers have a deep understanding of cloud platforms, emerging threats, and best practices, allowing them to design and implement tailored security measures that cater to the specific needs of each organization. This will enable organizations to focus on their core business activities while ensuring the security of their cloud assets.
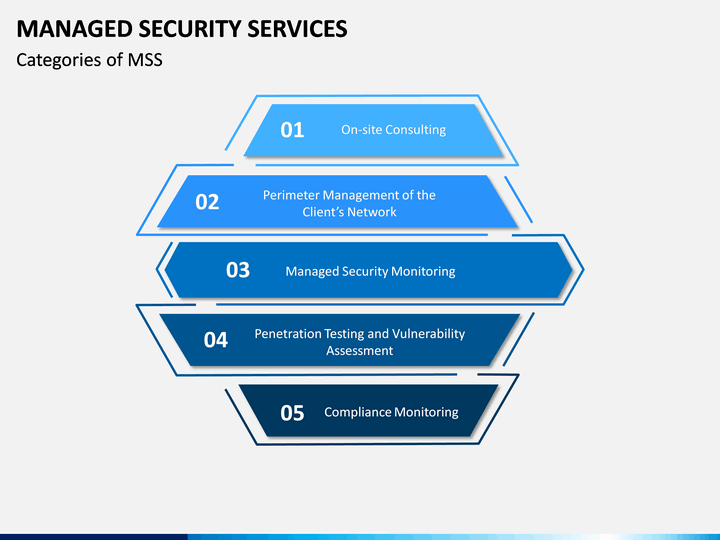
MSS categories
Understanding Managed Cloud Security Services
Managed cloud security services, or cloud security services, are outsourced security services offered by specialized providers known as managed security service providers (MSSPs). These services are designed to address the unique security challenges and risks associated with cloud computing.
A key component of managed cloud security services is the assessment and improvement of an organization's security posture. This involves evaluating the organization's current security measures, identifying vulnerabilities and weaknesses, and implementing solutions to strengthen security. By continuously monitoring the cloud environment and responding to security incidents in real-time, managed cloud security services help organizations maintain a strong security posture and protect against emerging threats.
In a cloud environment, security threats can come from various sources, including unauthorized access, data breaches, and malware attacks. Managed cloud security services employ multiple tools and techniques to detect and mitigate these threats. This includes deploying firewalls to protect against unauthorized access, implementing intrusion detection systems to identify potential breaches, and using threat intelligence to stay ahead of emerging threats.
One key advantage of managed cloud security services is the ability to leverage the expertise of MSSPs. These providers have specialized knowledge and experience in cloud security and can offer insights and guidance to organizations. They can help organizations navigate the complex landscape of cloud security, stay updated on the latest security trends and best practices, and ensure compliance with industry regulations.
Defining Managed Cloud Security
Managed cloud security, or cloud security management, refers to the outsourced management and monitoring of an organization's cloud security measures. In this model, a managed security service provider (MSSP) takes responsibility for securing the organization's cloud resources and protecting sensitive data from unauthorized access.
Cloud resources, such as virtual machines, storage, and networks, are essential components of a cloud environment. These resources must be secured to prevent unauthorized access and protect sensitive data. Managed cloud security services provide the expertise and tools necessary to manage these resources and ensure their security.
Sensitive data, such as personally identifiable information (PII) or financial records, often resides in cloud environments. This data needs to be protected from unauthorized access to maintain the organization's and its customers' privacy and integrity. Managed cloud security services implement encryption, access controls, and other security measures to safeguard sensitive data from unauthorized access.
By outsourcing cloud security management to an MSSP, organizations can leverage the expertise and resources of a specialized provider. These providers have the knowledge and experience to implement robust security measures and protect against emerging threats.
The Scope of Services Offered
Managed cloud security services offer many services to help organizations maintain a secure cloud environment. These services include incident response, disaster recovery, firewall, and access management.
Incident response is a critical component of managed cloud security services. In the event of a security incident, such as a data breach or unauthorized access, the managed security service provider (MSSP) takes immediate action to mitigate the impact and restore the cloud environment's security. This includes investigating the incident, containing the threat, and implementing measures to prevent future incidents.
Disaster recovery is another essential service offered by managed cloud security providers. This involves creating and implementing a plan to recover data and restore operations in a catastrophic event or system failure. The MSSP works closely with the organization to develop a comprehensive disaster recovery strategy that ensures the continuity of business operations.
Firewall management is essential for maintaining the security of the cloud environment. Managed cloud security services include managing and configuring firewalls to protect against unauthorized access and network-based attacks. The MSSP ensures the firewall rules are current and align with the organization's security policies and regulatory requirements.
Access management is crucial for controlling who has access to the cloud resources. Managed cloud security services implement and manage access controls, such as multi-factor authentication and role-based access control, to ensure that only authorized users can access the cloud environment. This helps prevent unauthorized access and protects sensitive data from being compromised.
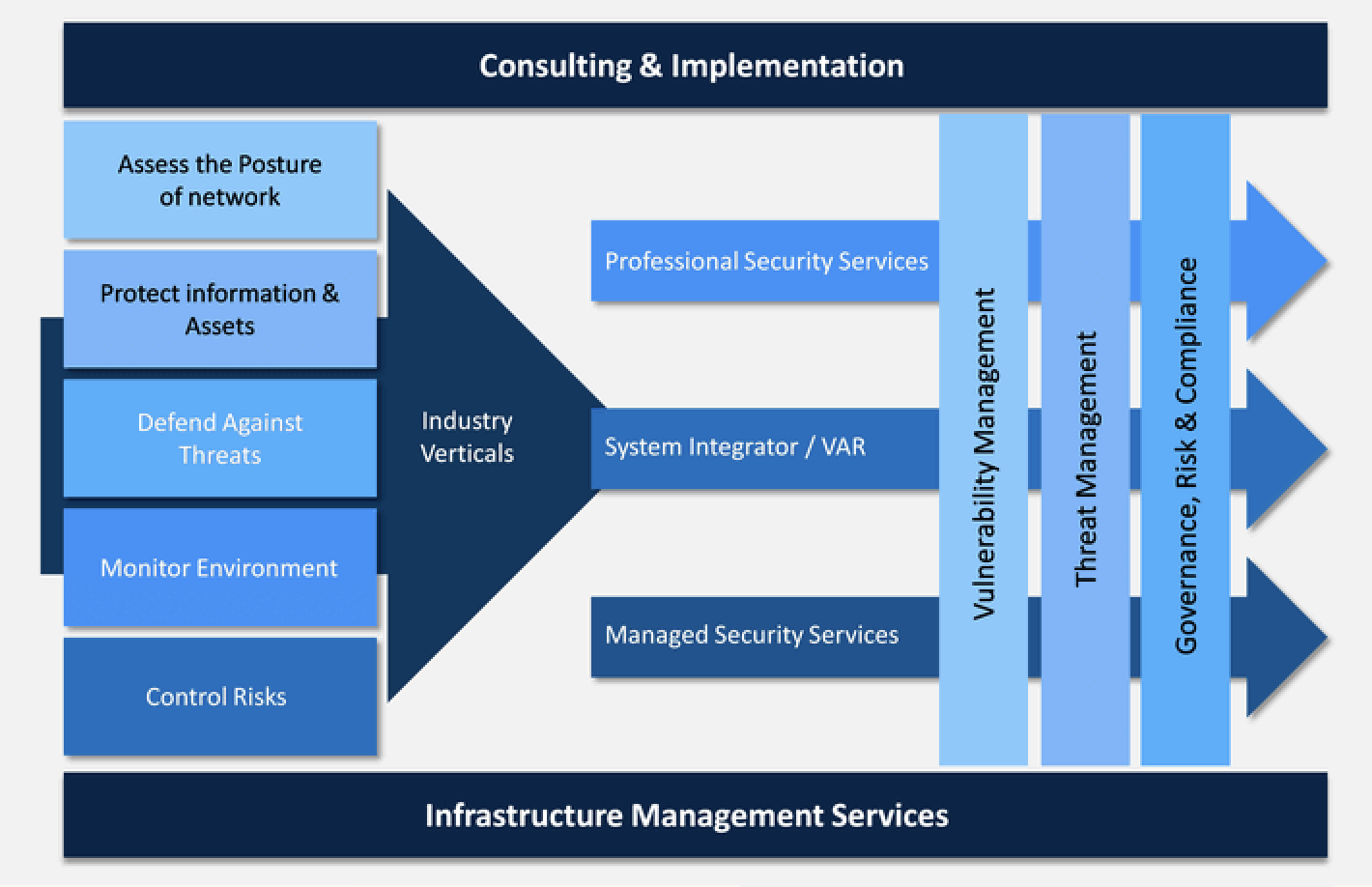
Key Categories of Managed Cloud Security Services
Managed cloud security services can be categorized into three key areas: network security, identity and access management (IAM), and threat intelligence and monitoring. These categories cover the essential components of cloud security and address the challenges and risks associated with cloud computing.
Network Security in the Cloud
Network security is a critical aspect of cloud security. As organizations increasingly rely on cloud infrastructure and services, securing the network becomes essential to protect against data breaches and other security threats.
Managed cloud security services provide comprehensive network security measures to safeguard the cloud infrastructure. This includes implementing firewalls, intrusion detection and prevention systems, and other network security tools to ensure that only authorized traffic can access the cloud resources. These measures help prevent unauthorized access and protect against data breaches and other network-based attacks.
Cloud security management involves monitoring the network for potential security risks and vulnerabilities. Managed cloud security services provide continuous monitoring and analysis of network traffic to detect and respond to security threats in real time. This proactive approach helps organizations stay ahead of emerging threats and ensures the security of their cloud infrastructure.
Identity and Access Management (IAM)
Identity and access management (IAM) is a crucial cloud security component. Managed cloud security services provide robust IAM solutions to control access to cloud resources, ensure regulatory compliance, and protect sensitive data.
IAM solutions offered by managed cloud security providers include:
- Provisioning and de-provisioning user accounts: Ensuring users have the appropriate access to cloud resources based on their roles and responsibilities.
- Multi-factor authentication (MFA): Adding an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a unique token.
- Single sign-on (SSO): Allowing users to access multiple cloud applications and services with a single set of credentials.
- Identity federation: Enabling users to authenticate using their existing corporate credentials, reducing the need for multiple sets of usernames and passwords.
- Role-based access control (RBAC): Assigning permissions and access levels to users based on their organizational roles and responsibilities.
- Audit and compliance reporting: Providing detailed reports on user access and activity for compliance purposes.
These IAM solutions help organizations ensure that only authorized users have access to cloud resources, protecting sensitive data and ensuring regulatory compliance.
Threat Intelligence and Monitoring
Threat intelligence and monitoring are critical components of managed cloud security services. These services provide organizations the tools and expertise to detect and respond to security threats in real-time.
Managed cloud security services leverage threat intelligence to stay ahead of emerging threats. Threat intelligence involves collecting and analyzing information about potential threats and security vulnerabilities. This information is used to develop proactive security measures and implement controls to mitigate the risks.
Monitoring is an essential aspect of managed cloud security services. Continuous monitoring of the cloud environment allows organizations to detect and respond to security incidents promptly. Managed cloud security services employ advanced monitoring tools and technologies to analyze network traffic, detect anomalies, and identify potential security threats. This enables organizations to take immediate action to mitigate the impact of security incidents and protect their cloud resources.
Visibility is a crucial benefit of managed cloud security services. By continuously monitoring the cloud environment, organizations gain visibility into network traffic, user activity, and potential security risks. This visibility allows organizations to make informed decisions, implement necessary security measures, and respond effectively to security incidents.
Overall, threat intelligence and monitoring are crucial for maintaining the cloud environment's security. Managed cloud security services provide organizations with the tools and expertise to stay ahead of emerging threats, detect security incidents in real time, and ensure the continuous protection of their cloud resources.
Use Cases Demonstrating the Value of Managed Cloud Security
Managed cloud security services provide value to organizations across various industries and use cases. Here are a few examples:
Enhancing Compliance in Financial Services
In the financial services industry, regulatory compliance is of utmost importance. Managed cloud security services help financial institutions meet regulatory requirements and ensure the security of their sensitive data. By implementing robust security measures and continuous monitoring, managed cloud security services enable financial institutions to enhance compliance and protect against data breaches. This allows them to build trust with their customers and maintain a strong reputation in the industry.
Protecting Healthcare Data through IAM
In the healthcare industry, protecting sensitive patient data is crucial. Managed cloud security services offer IAM solutions that enable healthcare organizations to control access to patient data and ensure compliance with HIPAA regulations. By implementing robust authentication methods and role-based access controls, managed cloud security services help healthcare organizations protect sensitive data from unauthorized access. This ensures patient privacy and helps healthcare organizations maintain compliance with regulatory requirements.
E-commerce Fraud Prevention
E-commerce businesses face the constant threat of cyber-attacks and fraud. Managed cloud security services help e-commerce businesses prevent unauthorized access and protect against cyber threats. By implementing robust security measures such as firewall management, intrusion detection systems, and real-time monitoring, managed cloud security services help e-commerce businesses detect and prevent fraudulent activities. This ensures the security of customer data, builds trust with customers, and protects the reputation of the e-commerce business.
Secure Cloud Migration for Enterprises
Cloud migration is a critical step in many enterprises' digital transformation journey. Managed cloud security services offer expertise and best practices to ensure a secure and successful cloud migration. By conducting risk assessments, implementing security controls, and providing continuous monitoring, managed cloud security services help enterprises securely migrate their applications and data to the cloud. This enables enterprises to leverage the benefits of cloud technology while mitigating the risks associated with cloud migration.
Evaluating Your Managed Cloud Security Needs
Evaluating your organization's managed cloud security needs is crucial to ensure that the chosen service provider aligns with your requirements.
Assessing Your Security Posture
Assessing your organization's security posture is the first step in evaluating your managed cloud security needs. This involves identifying vulnerabilities, assessing existing security measures' effectiveness, and conducting a risk assessment. By understanding your organization's security strengths and weaknesses, you can determine the level of support and expertise required from a managed cloud security service provider.
Identifying Gaps in Existing Security Measures
Identifying gaps in your security measures is essential to determine the areas where additional support is needed. This involves evaluating past security breaches, incident response effectiveness, and conducting a gap analysis.
Selecting the Right Managed Cloud Security Provider
Selecting the right managed cloud security provider is crucial to ensure the effectiveness and success of your cloud security strategy.
Critical Considerations in Provider Selection
When selecting a managed cloud security provider, consider the following key factors:
- Managed Security Service (MSS) capabilities: Evaluate the provider's expertise in cloud security and their track record in delivering managed security services.
- Service Level Agreements (SLAs): Review the SLAs offered by the provider to ensure they align with your organization's security requirements.
- Technical support: Assess the provider's technical support, including response times and availability.
- Alignment with IT strategy: Ensure the provider's services align with your organization's IT strategy and long-term goals.
Questions to Ask Potential Providers
When evaluating potential managed cloud security providers, it is essential to ask the right questions to ensure they can meet your organization's specific needs. Here are some questions to consider:
- What is your approach to cloud security, and how does it align with our organization's cloud security strategy?
- What incident response solutions do you offer, and how do you handle security incidents?
- How do you ensure compliance with regulatory requirements, such as GDPR or HIPAA?
- Can you provide references from other clients in our industry who have used your managed cloud security services?
- How do you stay updated on the latest security threats and best practices in cloud security?
Implementing Managed Cloud Security Services
Implementing managed cloud security services involves seamlessly integrating security measures into your existing cloud environment. From deploying robust encryption protocols to setting up advanced threat detection mechanisms, every aspect must be carefully orchestrated. Ongoing monitoring and timely incident response solutions are vital to safeguarding your cloud resources effectively.
Steps for Integration and Deployment
The first step in implementing managed cloud security services is integrating and deploying security measures. This involves:
- Defining the project's scope and objectives: Clearly outline the goals and objectives of the implementation and deployment process.
- Developing a project plan: Create a detailed project plan that includes timelines, milestones, and resource allocation.
- Assigning project management responsibilities: Designate a project manager to oversee and coordinate the implementation and deployment process.
- Implementing security measures: Based on the project plan, deploy the necessary security measures, such as firewalls, intrusion detection systems, and access controls.
- Automating security processes: Leverage automation tools and technologies to streamline security processes and ensure consistent and efficient security management.
Best Practices for Ongoing Management
Ongoing management is crucial to maintaining the effectiveness of managed cloud security services. Implementing best practices for ongoing management ensures the continuous protection of the cloud environment.
Some best practices for ongoing management include:
- Cybersecurity awareness and training: Educate employees about cybersecurity best practices and the importance of data protection.
- Encryption: Implement encryption techniques to protect sensitive data in transit and at rest.
- USB device control: Control and monitor the use of USB devices to prevent data breaches and unauthorized access.
- Unrivaled visibility: Leverage advanced monitoring tools and technologies to gain visibility into the cloud environment and detect security threats.
- Regular security assessments: Conduct regular security assessments to identify vulnerabilities and address potential risks.
Future Trends in Managed Cloud Security
Managed cloud security services constantly evolve to keep pace with the changing threat landscape and emerging technologies.
The Rise of AI and Machine Learning
AI and machine learning are increasingly being incorporated into managed cloud security services. These technologies enable organizations to identify real-time anomalous activities and potential security threats. AI and machine learning algorithms can analyze large volumes of data and detect patterns that may indicate a security incident. This allows for faster and more accurate threat detection and response. Additionally, AI and machine learning can automate specific security tasks, such as identifying and blocking malicious traffic, further enhancing the efficiency and effectiveness of managed cloud security services.
Evolving Threat Landscapes
The threat landscape is constantly evolving, with cyber threats becoming increasingly sophisticated. For adequate security protection, managed cloud security services must adapt to these growing threats. This includes staying updated on the latest threat intelligence, implementing advanced security measures, and continuously monitoring the cloud environment for potential security risks.
Final Thoughts
Mastering managed cloud security services is crucial for safeguarding an enterprise digital asset in today's ever-evolving threat landscape. Understanding the scope of services, critical categories like network security and IAM, and evaluating your security needs are paramount. By selecting the right provider and implementing best practices, you can enhance compliance, prevent fraud, and secure your cloud migration effectively. Looking ahead, embracing AI, adapting to regulatory changes, and measuring success will be essential. Stay informed, stay secure - subscribe to stay updated on the latest trends and insights in managed cloud security services.
Frequently Asked Questions
What Makes Managed Cloud Security Different from Traditional Security?
Managed cloud security differs from traditional security because it explicitly addresses cloud services' unique challenges and risks. It considers the dynamic nature of cloud environments, the need for scalability, and the requirements of digital transformation initiatives. Managed cloud security also emphasizes continuous monitoring, automation, and proactive threat intelligence to ensure effective cloud security management.
How Do Managed Cloud Security Services Adapt to Regulatory Changes?
Use managed cloud security services to stay updated on regulatory changes and adapt security measures to ensure ongoing compliance. By continuously monitoring regulatory requirements, managed cloud security services can make necessary adjustments to maintain a strong security posture and ensure compliance with industry-specific regulations. For example, CrowdStrike's Falcon Cloud Security incorporates regular updates and compliance checks to address changing regulatory requirements.
Can Small Businesses Benefit from Managed Cloud Security?
Yes, small businesses can benefit from managed cloud security services. These services provide small businesses access to advanced security measures and expertise that would otherwise be cost-prohibitive. By outsourcing their security management to a managed security service provider (MSSP), small businesses can ensure the cost-effective protection of their cloud environment. Companies such as Cloud Hacks cater specifically to SMEs looking for this service offering.
How to Measure the Success of Your Managed Cloud Security?
Various security metrics, such as incident response time, the number of security breaches detected, and the effectiveness of monitoring and detection capabilities, can measure the success of managed cloud security. Regularly reviewing and analyzing these metrics can help organizations assess the effectiveness and value of their managed cloud security services.
Preparing for Future Security Challenges: What Steps Should Companies Take?
To prepare for future security challenges, companies should focus on proactive cybersecurity measures, such as implementing best practices for data protection, disaster recovery, and backups. Staying updated on emerging threats and adopting a proactive approach to security can help companies mitigate future security risks and ensure business continuity.
Until next time "Protect Yourselves and Safeguard each other"
--Sean